At VDA Labs we work with a variety of companies both large and small. During our engagements, we see many of the same reoccurring issues that allow us access to systems. To help combat these threats VDA Labs is starting a blog series we are calling “Low-Hanging Fruit”. Throughout this series VDA will be talking about the most common issues we see, along with how each issue can be combated. This article discusses why organizations need Multi-Factor Authentication (MFA) and some foibles we see around MFA implementations.
WHAT IS MULTI-FACTOR AUTHENTICATION AND WHY DO YOU NEED IT?
Multi-factor authentication is the process of requiring two or more independent authentication solutions before allowing a user to authenticate. By requiring multiple factors it makes it more difficult for an attacker to successfully use any data they gather through social engineering or open source intelligence (OSINT). Typically the authentication will fall into the one of three categories.
- Something you know
- Passwords
- PIN
- Secret Questions
- Something you have
- RSA token
- YubiKey
- Phone based software authenticators
- Something you are
- Fingerprints
- Iris recognition
- Facial recognition
MFA ALL THE THINGS!
One of the most common foibles we see with MFA implementations is inconsistent application of 2FA. It is common during penetration testing for VDA to find OWA or O365 with proper two factor enabled, but to then discover users with VPN or VDI access that do not require MFA in those locations. The same idea applies to administrative interfaces. VDA has seen general users with MFA, but no extra levels of protection on backup appliances or SAN management interfaces.
Most companies have important applications or software with sensitive data or configurations. The general rule of thumb should require each system should have its own MFA enabled, especially for administrative access. If a vendor doesn’t support it, make sure you make feature requests so that MFA features get visibility and eventually get added to the software or hardware you are managing. In the meantime, defense in depth is your only option there.
NOT ALL MFA IS CREATED EQUAL: DEFEATING MFA
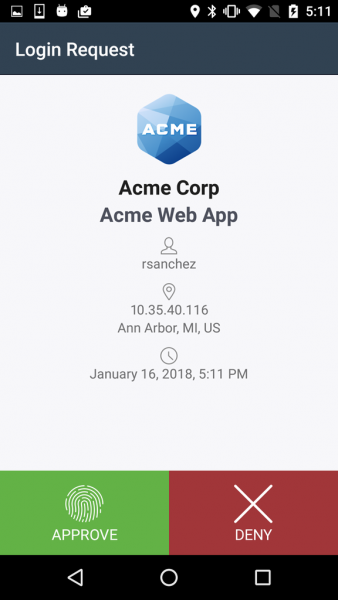
Although VDA is seeing MFA more each year, we have noticed some worrying trends, often allowing VDA to defeat certain techniques. The largest weakness VDA regularly sees is the use of push notifications for MFA. Although convenient, push notifications make it easy for attackers to spoof legitimate requests. These attacks can come in different forms. In the simplest form, attackers cause a push notification, hoping the user accepts the login attempt, regardless of the fact they didn’t recently perform a login themselves. The sneakier route is where the attacker tries to login around the start of the day or shift change so that it appears as if a second push notification was accidentally or redundantly generated. Users will sometimes just accept whatever.
The best and easiest defense against these push attacks is to disabling push notifications, and require one time passwords (OTP) for software based authenticators (the code you enter). By requiring users to use OTP, an attacker would need physical access to the phone or physical authenticator, so that they can enter the full login code the tools generate. A more complicate attack technique here is to spoof the SIM card of the users cell phone, if SMS is being used, such that attackers could still get the code. This only works for SMS. Thus, SMS is not nearly as secure, but we often seen many organizations, including banks using it. There have even been SIM vulnerabilities to compound this poor practice. All of these attacks require much more planning and physical access and greatly diminish the chances of an attack defeating your MFA setup. VDA would love to help your organization perform security testing of people, processes, or technology with this and other advanced techniques, contact us about a security analysis today.
Stay tuned for the rest of our series on low-hanging fruit. We eager to share ways that your organization can help create a more secure environment. Our next blog in this series will be about permissions, and how sprawl can be a major security concern for an organization.