EPSON Printer Vulnerabilities
The EPSON WF-2750 printer is a multi-functional printer for home and small office use. The printer has multiple connection points through Wi-Fi. Remote printing is one of the major features of this printer. Users can remotely print form mobile apps, web browsers, and cloud services. EPSON WF-2750 is compatible with EPSON iPrint mobile app. The Google Play Store ( https://play.google.com/store/apps/details?id=epson.print&hl=en ), shows over 10 million downloads for EPSON iPrint Android app. This indicates that large numbers of users may be using the app for remote printing. Although remote printing is a nice feature to users, it expands the attack surface of the product from the security point of view.
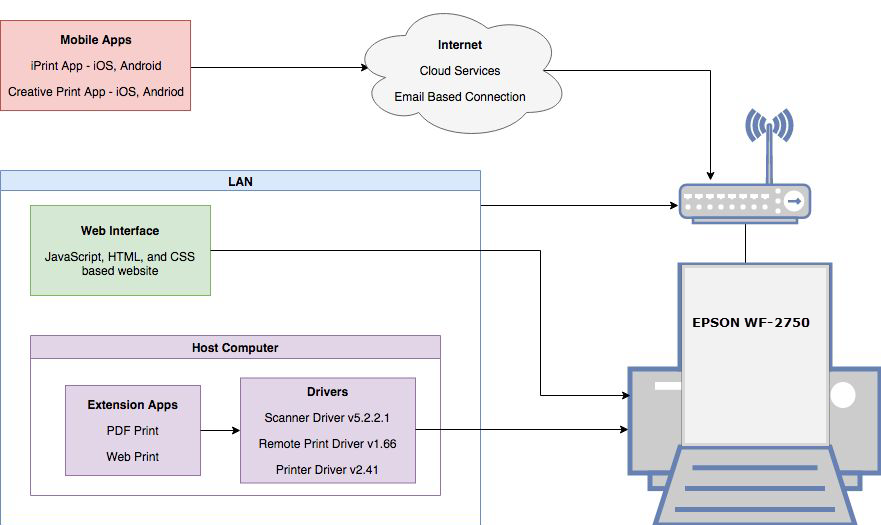
The following vulnerabilities have been discovered in a research conducted on EPSON WF-2750 printer:
1. Insecure ContentProvider
Affected Application: EPSON iPrint Android App
Version: App version: 6.6.3
Summary: The ContentProvider in the EPSON iPrint application 6.6.3 for Android does not properly restrict data access. This allows an attacker’s application to read scanned documents.
CVE Id: CVE-2018-14902
Details:
The Android EPSON iPrint app enabled the ContentProvider export setting in the AndroidManifest file. Android ContentProvider allows other apps on the device to share data. Improper implementation of ContentProvider could cause data to be accessed by attacker’s app. The EPSON iPrint app allow users to scan documents directly from their device. However, the scanned documents are not properly protected by the app due to insecure implementation of Android ContentProvider feature in the app. As shown in the figure below a malicious app can access the scanned document when iPrint app is used to scan documents. The below figure shows EPSON iPrint app (left) and a test app (right) showing a scanned document image.
 |
 |
Remediation:
If there is no intention to share data to other apps, disable ContentProvider export feature by marking android:exported=false in the application manifest file. If data sharing is necessary, specify only required permission levels. For instance, if the data sharing is between EPSON owned apps, signature protection could be used to limit data sharing between the apps signed by the same key. This can be achieved by setting android:protectionLevel to signature. More information can be found on Android security tips page (https://developer.android.com/training/articles/security-tips).
2. Insecure Firmware Update
Affected Application: EPSON WF-2750 Printer / Firmware
Version: Firmware version- JP02I2
Summary: EPSON WF-2750 JP02I2 printers do not properly validate files before running updates, which allows remote attackers to cause a printer malfunction or send malicious data to the printer.
CVE Id: CVE-2018-14903
Details:
The EPSON Printer comes with a firmware updater executable (EPFWUPD.exe), which is responsible for sending the updated firmware file to the printer. The printer starts processing as soon as the update file is received. The firmware updater uses the HTTP protocol to send the update file to a specific path on the device. Due to insecure communication and insufficient data validation on the printer an attacker can remotely send malicious data to the printer connected to the network. 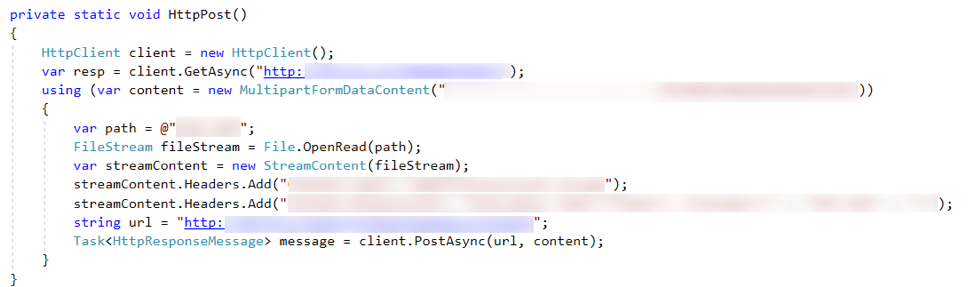
Remediation:
To prevent unwanted data transfer, the printer should verify the request before accepting and processing. This could be achieved using secure communication between the host computer and the printer, and by data validation before processing.
3. Insecure API Keys
Affected Application: EPSON iPrint Android App
Version: App version: 6.6.3
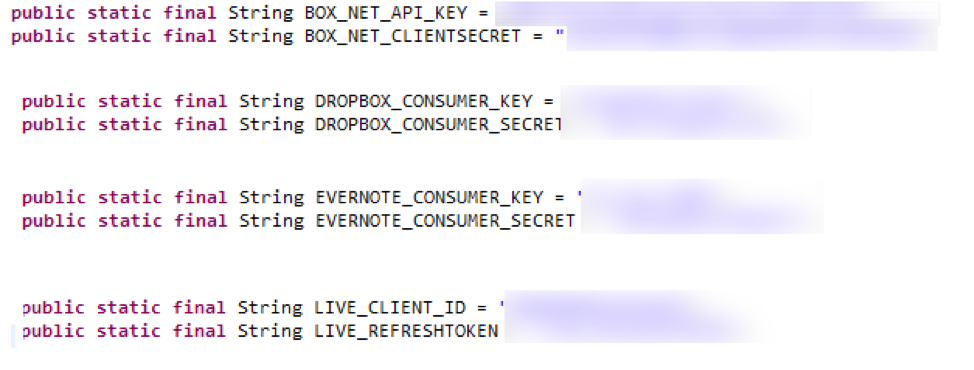
Summary: The EPSON iPrint application 6.6.3 for Android contains hard-coded API and Secret keys for the Dropbox, Box, Evernote, and OneDrive services.
CVE Id: CVE-2018-14901
Details:
The EPSON iPrint Android app uses third-party components such as Box, Dropbox, Evernote, Google Ad, Google Drive, and OneDrive. No code encryption or no obfuscation technique is used in the app. The third party API keys are stored in the app without proper encryption mechanism. Consumer credential safety and phishing attacks are possible threats due to exposing these keys.
Remediation:
When possible, provide third party services from secure servers and let the app communicate to the server instead of using the app hosting such services. Or use commercial obfuscators, store API keys in a secure server, and make separate calls to access the keys on demand.
4. Cross Site Printing (XPS)
Affected Application: EPSON WF-2750 Printer Firmware
Version: Firmware version- JP02I2
Summary: On EPSON WF-2750 JP02I2 printers, there is no filtering of print jobs. Remote attackers can send print jobs directly to the printer via TCP port 9100
CVE Id: CVE-2018-14900
Details:
Internet Printing Protocol (IPP) is enabled by default on port 631. As shown in figure below, non-secure communications are not allowed in the setting. And only port 631 is set as IPP.
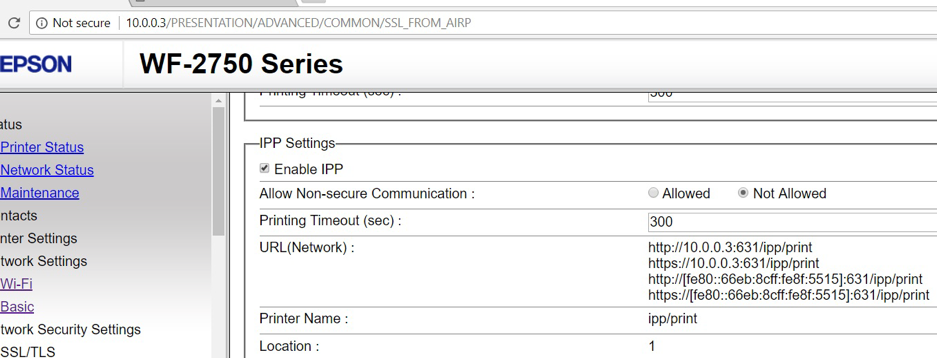
With this setting, the printer refuses non-secure (http) requests with port 631. However, the printer is able to accept remote print jobs with non-secure communication channel via port 9100 and successfully prints the given payload text.
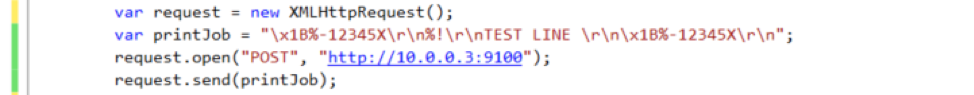
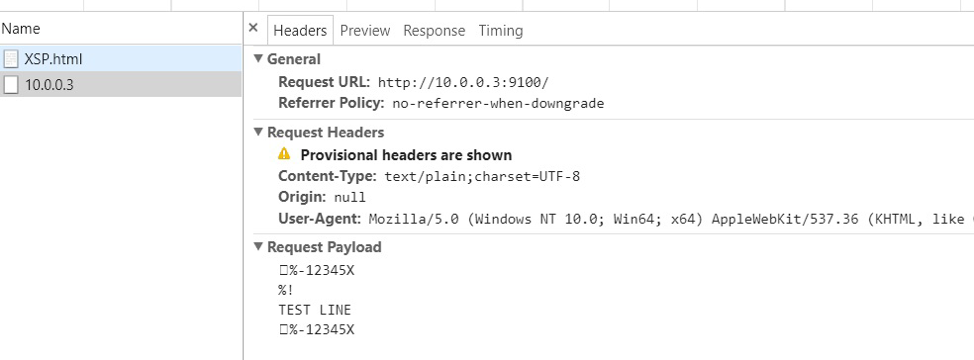
Remediation:
Disabling port 9100 by default would be a quick fix. If using port 9100 is necessary, each request needs to be validated. Data sanitization may also be necessary before processing, as payloads may contain injected commands.
5. HTML Injection
Affected Application: EPSON WF-2750 Printer / Web Interface
Version: Prior to Firmware version- JP02I2
Summary: On the EPSON WF-2750 JP02I2 printer, the Web interface AirPrint Setup page is vulnerable to HTML Injection that can redirect users to malicious sites.
CVE Id: CVE-2018-14899
Details:
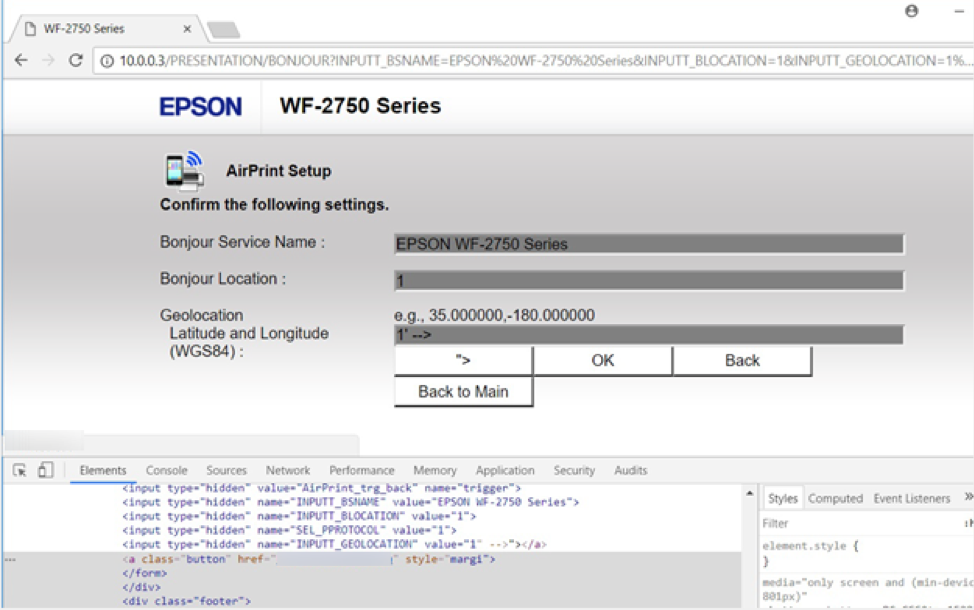
The printer web server fails to properly check the validity of the HTML form before processing. The following sample shows HTML injection on the AirPrint Setup page. The INPUTT_GEOLOCATION parameter can accept HTML code. This could lead injecting malicious links to the page.
http://10.0.0.3/PRESENTATION/BONJOUR?INPUTT_BSNAME=EPSON WF-2750 Series&INPUTT_BLOCATION=1&INPUTT_GEOLOCATION=1' -->"><a class='button' href='http://xxxxxxxxxxxxx' style = 'margin: 242px 0 0 -242px; position: relative;'>OK</a>&SEL_PPROTOCOL=1&trigger=AirPrint_trg_set&tm=1
The above injection hides the original OK button and shows the custom OK button which directs users to different location.
Remediation:
XSS vulnerability can be prevented by sanitizing all user inputs, data validation, request validation, HTML encoding, JavaScript escaping, etc. More detailed information on how to prevent XSS attack can be found on OWASP site (https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html)
Summary:
One thing that is worth noting: we tried and tried to reach out to Epson. We contacted staff on LinkedIn. We pinged Epson on Twitter. We looked for a “[email protected]” mailbox. We could find no one to submit these two. It was suggested to us that we point Epson to processes like: https://first.org/education/FIRST_PSIRT_Service_Framework_v1.0″ target=”_blank” rel=”nofollow noopener noreferrer”>https://first.org/education/FIRST_PSIRT_Service_Framework_v1.0 But we didn’t know who to tell. We ran out of time to search further for someone to submit these to, and in the end, we decide to blog about these bugs.
